You can try this method if you meet one of the following situation:
- You have a public IP to the internet (both static and dynamic IPs should work, but you should need DDNS service if you don’t have static IP)
- Your ISP restricts 80 or 443 access to the internet (like in China)
- You don’t want hacks or some tricky commands on Unifi Cloud Key like HOWTO: Install Signed SSL Certificate on Cloudkey and use for secure portal or Setting up HTTPS on the UniFi CloudKey
. (Both require install CA issued certificates on UCK)
Requirements
- A public IP to the internet (to access Unifi Security Gateway remotely)
- A server running Nginx on public internet
- A CA issued certificate
Set port forwarding for your Cloud Key
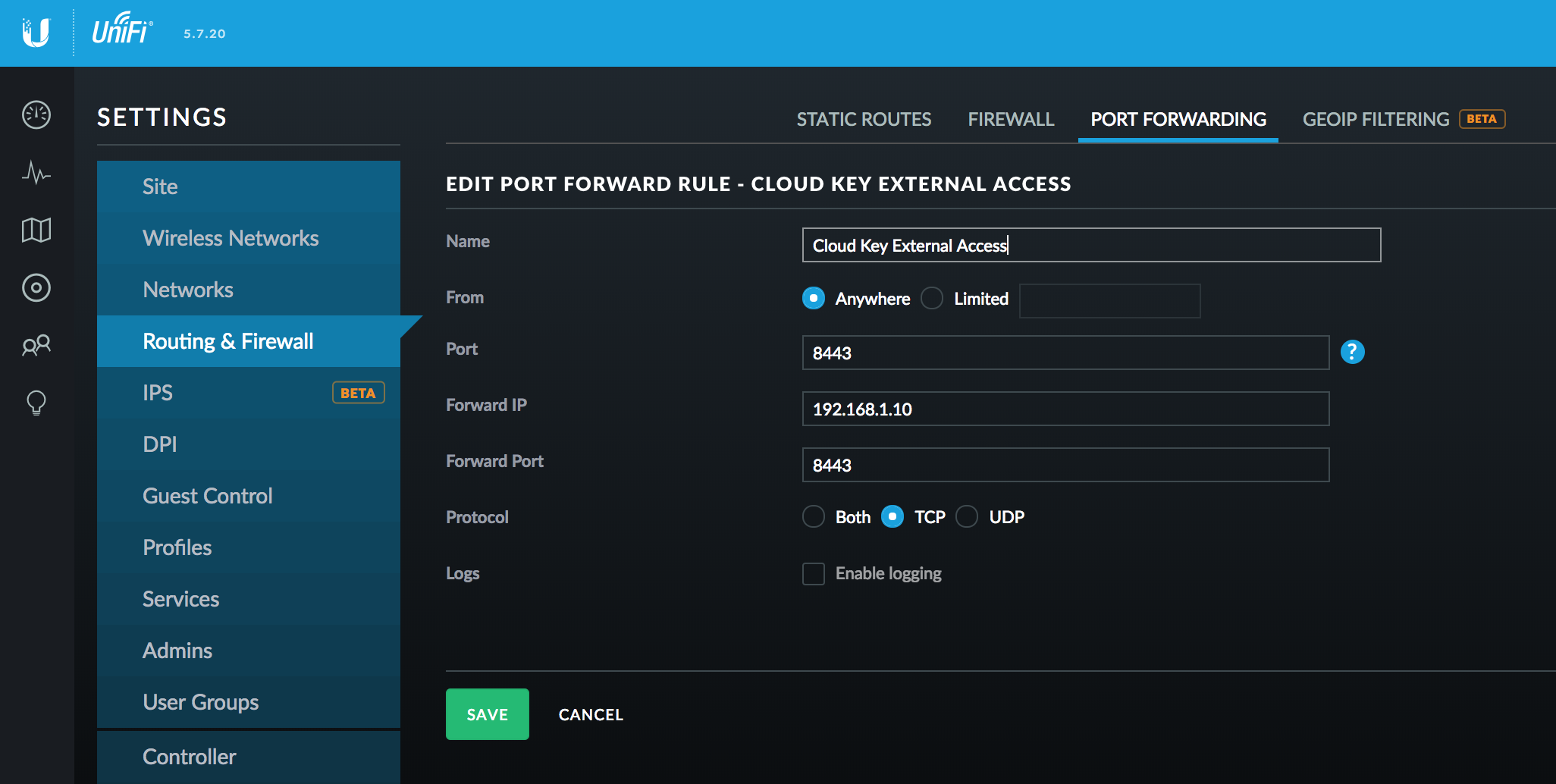
In general, you can access your Unifi Secuiry Gateway (USG) via your public IP (USG_IP), so in my method you need to forward your UCK management dashboard (UCK_IP:8443 by default) traffic to your public IP. it’s under Settings – Routing & Firewall – Port Forwarding. Enter your Cloud Key address IP as Forward IP, use default 8443 as Port and Forward Port. You can also limit from destination to your server IP for security best practice.
Setup Nginx proxy
Use the following Nginx configuration, please note that this is a simplified version.
server {
listen 80;
listen [::]:80;
server_name unifi.example.com;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
# To avoid unreachable port error when launching dashboard from unifi.ubnt.com
listen 8443 ssl http2;
listen [::]:8443 ssl http2;
server_name unifi.example.com;
# Certificate
ssl_certificate /etc/nginx/ssl/unifi.example.com.crt;
ssl_certificate_key /etc/nginx/ssl/unifi.example.com.key;
location /wss {
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
proxy_set_header CLIENT_IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_read_timeout 86400;
proxy_pass https://USG_IP:8443;
}
location / {
proxy_set_header Host $http_host;
proxy_set_header CLIENT_IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_read_timeout 180;
proxy_pass https://USG_IP:8443;
}
}
Update DNS records
Point your unifi.example.com to your public IP. Access it in your browser and everything now should works!